
Jon Atkinson08/09/21
8 min read

Website security has become a major concern for charities as cyber attacks increase and become more advanced.
Cyber crime shot up 600% as a result of the pandemic as we worked and shopped from home with ransomware attacks happening every 11 seconds.
The cost to the global economy is predicted to reach $10.5trillion by 2025 yet the threat of attacks is still not taken as seriously as it should be.
Despite 68% of charity leaders listing online security as high priority, less than a third of third-sector organisations in the UK have carried out a cyber risk assessment and the number of individuals with a specific responsibility for cyber security has actually dropped.
Whatever the reasons for these contradictions, the threat remains real and charities need to have robust systems and practices in place to keep their organisations and the data they hold secure.

The UK Government's National Cyber Security Strategy divides cybercrime into two:
So when considering your charity’s cyber security systems and protocols you’ll be focusing on the first point.
Techniques used by criminals vary and while most are considered low-skilled, they can gain access to sophisticated tools through their networks and via the Dark Web.
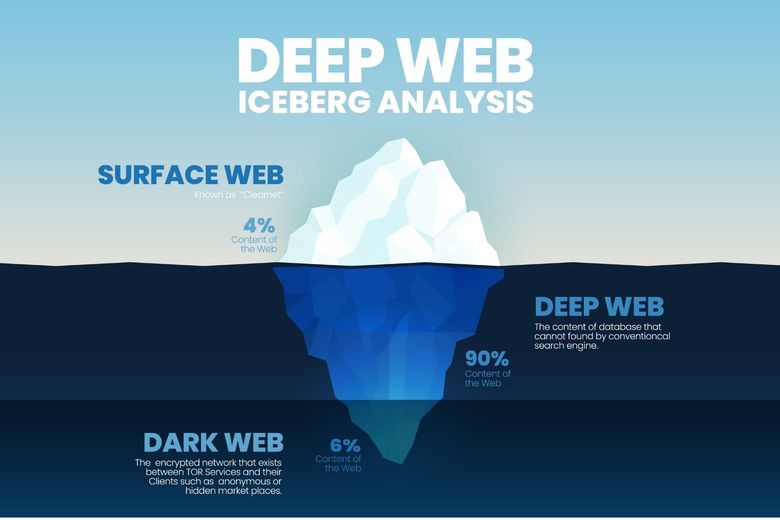
Attacks are not always targeted, either. Random, automated ones are commonplace; we’ve all received spurious phishing emails, for example, which are designed to encourage us to download something which appears to be harmless but is indeed malicious.
Hackers use a variety of methods to disrupt or infiltrate systems and while you don’t need to understand these in detail, it is worth being aware of them.
The most common is malware, short for malicious software, and comes in many forms including viruses, worms, ransomware and trojans.
It is often introduced into a system by those phishing emails or by downloading something from a less-than-trusted source on the web. It can also be installed on to a website via a range of attacks.
Malware spreads between computers, can delete files, cause system crashes and be used to steal personal data.
As a result, financial data can be used to steal individuals’ money, the data can be sold to a criminal organisation, organisations can be held to ransom before their systems are restored or future online activity can be monitored and actions, such as keystrokes, captured.

In 2020, a number of charities were hit and personal data stolen after a breach at Blackbaud, a company providing technology solutions to the sector. It just goes to show that even leading names in technology are vulnerable.
If malware is installed on to a website, search engines can flag to users that it has been compromised. This can result in a loss of traffic, online donations, service downtime, a reduction in search visibility and even restrict access via the Google Chrome browser.
Another common attack is called a Denial of Service, or DoS, and its intention is to make a machine or resource - for example, a website - unavailable to users.
Hackers can also implement a Distributed Denial of Service (DDoS) attack. This is where a server is flooded with so many requests that it ceases to operate, thus taking down all websites and services residing on it.

Beyond a shadow of a doubt, prevention is better than cure. Picking up the pieces after an attack can be costly and time-consuming while the worst case scenario is an organisation’s demise.
Indeed, more than 1million businesses would collapse if hit by a serious cyber attack.
It means having robust systems and processes in place is essential, and this should include regular assessments, communications and staff training. Relying on an individual to send an ad-hoc message to all users when receiving a suspect email frankly isn’t good enough.
First off, consider the platform your website is built on. If it’s WordPress then you’ve immediately got an amber, if not red, flag.
It’s reported that 30,000 websites are successfully attacked every day - and 90% of hacked CMS-powered websites are hosted by WordPress.
One common technique hackers use is a brute force attack, where combinations of username and passwords are tried to gain access to the admin, back-end of a website.
WordPress sites make life incredibly easy for hackers by simplifying the URL in order to get access to the back-end sign-up page. All you need to do is add /wp-admin to your domain and you’re there. Then, the brute force attacks can begin.
This is just one of the reasons why we believe Django is a better option for charities than WordPress.

If you are running your site on WordPress - and it is suitable for many organisations - make sure you have a strong admin password. Contrary to some advice, the National Cyber Security Centre says passwords don’t need changing unless there’s been a breach.
Also, it’s absolutely critical that you change manufacturer passwords when first signing in to a new system. Many organisations and individuals have fallen foul of retaining failing to change the likes of username = admin and password = password123.
If you’ve got a number of passwords for different systems you should consider storing them in a specialist password manager. We’ve known of organisations which keep passwords on a spreadsheet titled ‘Passwords’ on their internal server. If a hacker gets into your system, it’s not going to be a challenge finding this file.
Where possible, we’d wholeheartedly recommend applying two-step authentication. This is where successful sign-in details are given and a code is then sent to another device for confirmation. A hacker might get your sign-in details but this will prevent them gaining system access.

To guard against malware attacks you’ll need to ensure you have the basics in place while also staying on top of some important areas.
If you’re working from the office, your organisation should make sure the firewall is operational and switched on while all machines should be running anti-virus.
Only ever install approved software or restrict users’ ability to run their own downloads. This is common in larger organisations, with only administrators being able to carry out this function.
An area which can be missed is updating systems. A lot of technology is updated, or patched, regularly - to add new features, fix bugs and improve usability - and you should stay on top of these.
Failing to do so can make you more vulnerable, and this has been one of WordPress’ weakest points for years.
It’s also a good idea to consider very carefully the usage of USB devices and other removable media - are they really required? Or is using the cloud a better alternative?

Nearly all successful cyber attacks are as a result of human error. It means continual and regular staff education should be marked in your calendar.
If you make them interactive and try to inject a bit of fun, rather than taking a holier-than-thou approach, you should encourage buy-in and your points will stand a better chance of sticking.
Provide examples of phishing emails and go through ways of spotting them, for example poor spelling and grammar, requesting sensitive information, containing odd attachments.
Phishing techniques are becoming more advanced and emails can mimic staff addresses and even signatures, so educate your team to not share sensitive info via email. That way, if a colleague asks for financial info or similar you know not to reply to the email, but report it following your organisation’s protocol.
Find examples and listen to how your teams would react if they received what looks like a legitimate request for sensitive information. If they’re unsure or would provide the asked-for information then you know you need to keep banging the security drum.

Admittedly, this can feel a drag, particularly during a busy day or week, but backing up your data is super important for any organisation. If you are unlucky enough to be hit by an attack, this will make restoring data and ensuring organisational continuity much easier.
And remember that you can automate your data back-up.
The frequency of back-ups is entirely your call but once a day or once a week - depending on the size of your charity - is a good place to start.
Again, have a look to the cloud for back-up options.

If you have - or suspect you have - been attacked, the first thing to do is contact your IT team, whether that’s internal or external.
Let them deal with it or talk you through necessary steps. Unless you have experience of dealing with a hack, don’t try to sort yourself or you could make things worse.
Then think about your communications with all stakeholders - staff, donors, beneficiaries, volunteers and more.
If their data has fallen into the wrong hands they deserve to be told and can take their own actions as a result, for example they may want to change passwords for other sites.
Keep them informed as you learn more and, while they will be concerned or even angry to begin with, updating them regularly shows that you’re taking the breach seriously and that you care about them.
Contact the authorities. Police might be able to follow up on the attack, and you might be in breach of GDPR so the earliest the Information Commissioner’s Office (ICO) can learn of the breach the better. They might even be able to support you in your recovery from it.
Finally, go back to the education piece. The hacker got in somehow but don’t be judgmental in sessions as the aim is to make your team feel supported and ready to combat future attacks.
Reiterate the principles, the basics and the practical steps your team needs to take.

Data breaches exposed 36 billion records in the first half of 2020. Cyber crime is growing, the Dark Web is part of everyday conversations and hacking techniques are advancing.
Remote working has become a particular target for hackers and there remains a significant cyber security skills gap, with human error accounting for the vast majority of breaches.
So get your systems, processes and staff up to scratch.
Online security is like a sports umpire or referee: you don’t notice it when it’s doing its job well, but it becomes the centre of attention through poor performance.
Don’t let it be your charity’s talking point.